The world of work has changed significantly in the last six months with millions of employees now working from home. Perimeter defences that businesses previously relied on are proving insufficient because the controls that were applied when employees were predominantly office-based, with approved devices connected to the network, do not work as well for a distributed workforce. Many organisations are now finding that Zero Trust Security offers a better approach.
What is Zero Trust?
Zero Trust is a security concept that requires all users to be authenticated, authorised and have their security configuration and posture continuously validated, before being granted access to applications and data.
The concept was introduced by Forrester Research over a decade ago but is more relevant than ever.
Zero Trust uses a variety of advanced technologies that are able to continuously monitor and validate that a user and device have the right privileges and attributes. Organisations must ensure that all access requests are also continuously verified prior to allowing a connection to any enterprise or cloud asset. The policies rely heavily on real-time visibility of attributes such as:
- User identity
- Endpoint hardware
- Patch levels
- Vulnerabilities
- Applications installed
- Security or incident detections
Why Zero Trust is important
Zero Trust is one of the most effective ways for organisations to control who and what has access to their networks, applications and, more importantly, data. Adding preventative measures like next generation firewalls, often called the micro-perimeters or micro-segmentation, can effectively segregate and manage the network.
This will help deter attackers and limit access in the event of a breach. It is a critical layer of security that organisations require when they have a remote or global workforce with a growing number of endpoints.
‘Never trust, always verify’ principle
Zero Trust is a methodology, not a tool or a product.
At its heart is the simple concept: do not trust anybody operating inside your network and, instead, make them continuously authenticate their identity. It is targeted at both attackers outside of the network that have breached it and malicious insiders. The aim being to prevent them moving laterally through the network as they seek out sensitive data.
The importance of this approach was demonstrated in the case of Edward Snowden, the American whistle-blower who copied and leaked highly classified information from the National Security Agency (NSA) in 2013.
Snowden had legitimate credentials to operate as a subcontractor within the National Security Agency (NSA) network. Once he was granted access there was no further authentication procedures and he was able to download top-secret material.
Had Zero Trust with its core principles of least privilege and real-time monitoring of malicious activities been in place, it is likely that he would have been discovered earlier.

Key principles of Zero Trust Security
There are a number of key principles behind a robust Zero Trust policy, which are explored below:
Know your Architecture – including users, devices and services
It is critical to have comprehensive information about your assets. In order to get benefit from a Zero Trust approach, you need to know about each component of your architecture – from users and their devices, through to the services, applications and data they are accessing.
There are several pre-requisites that must be considered:
- Storing component information in a centralised place
- Business process mapping
- Identifying all potential connection points — both physical and virtual
- Determining if the device accessing your services is up-to-date, compliant with your device configuration policies and in a healthy state
Together, these represent some of the most important signals used to control access to services and data. Having policies that govern the above, in a place where they can easily be managed, reviewed, and updated are fundamental to the success of a Zero Trust environment.
Services also need to be kept up to date with the latest software patches. You need to be able to determine the version and patch level of the service you are using and, it goes without saying, that patches fixing vulnerabilities should be applied at the earliest opportunity. Identifying and prioritising patching can minimise the effect of users suffering from ‘patch fatigue’ and ensures that the most vulnerable devices are at the highest patch levels.
Create a strong device identity
Each device should be uniquely identifiable in a single device directory. This enables efficient asset management and clear visibility of the devices which access services and your data. This will help when applying policies and compliance as well as managing the health of the device estate.
Leverage a variety of preventative technologies
Multi-factor authentication (MFA) is a major requirement for a Zero Trust architecture. But it should be implemented in a way that does not hinder the use of the service. Therefore, it is important to select where additional authentication points are or where additional authentication factors are used. For example, authentication should be used when requests are high impact or important, or when the user is accessing sensitive data or requesting privileged actions, such as creating or deleting users.
To enable granular access control, specific roles for each user should be created. Then ensure the access control and device directory can be employed by all the services you plan to use, both internal and external. This will also allow the organisation to use least privilege access, granting the user and devices the lowest level of access required in order to carry out their role.
The micro segmentation technique can be used to create small zones within the network to help maintain separated access to different parts of the network. This could be invaluable in helping to contain an attack if a breach occurs.
Focus on monitoring devices and services
Organisations should also incorporate real-time monitoring capabilities to improve their “breakout time” — the critical window between when an intruder compromises the first machine and when they can move laterally to other systems.
Real-time monitoring is essential to the organisation’s ability to detect, investigate and remediate intrusions. Automation and orchestration can also be a benefit here in helping remediation to take place quickly if an attack or breach is identified.
Set policies according to value of the service or data
The power of a Zero Trust architecture comes from the access policies that you define. These policies can consider several signals from the connection in real-time and from the signals database to a build context for the connection. This context is then used to gain confidence in the connection request and decide if it is trusted enough to continue. The role of the Policy Engine performs this policy evaluation and decision.
Focus on the broader security strategy, not just the technology
A Zero Trust architecture is just one aspect of a comprehensive security strategy. Whilst technology plays an important part in protecting the organisation, digital capabilities alone will not prevent breaches. Companies must adopt a holistic security solution that incorporates a variety of endpoint monitoring, detection and response capabilities to ensure the safety of their networks, but another challenge is getting staff to think along new lines. Moving to a Zero Trust architecture takes time and should be part of the organisations digital transformation strategy involving the CISO, CIO and others at this level so they can prioritise the actions needed to move to this operating model.
Audit everything!
While not a glamorous activity, auditing should be a central part of your security strategy. With a documented record of all actions performed by a user, these data sets can be used in forensic analysis and help to identify suspicious activity in real-time with the option to terminate sessions. In addition, audit data can be leveraged to prove compliance, with reports on every user’s privileges and associated activity.
How can you leverage ServiceNow to achieve Zero Trust Security?
Achieving all of the above is not easy. But there are a number of ways ServiceNow can help. The diagram below shows some of the key points.
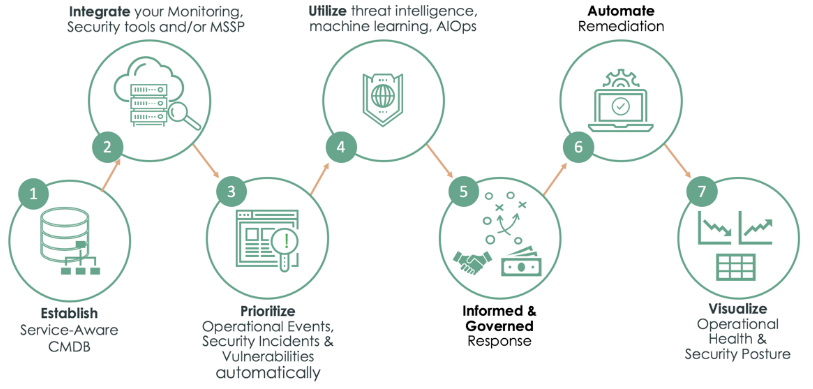
The architecture
ServiceNow’s configuration management database (CMDB) and IT Operations Management (ITOM) capabilities provide device, service and asset visibility. The CMDB allows you to build logical representations of assets, services, and the relationships between them to develop a better understanding of your organisation’s architecture. Using ServiceNow we can build relationships to the assets and services to the users who have access or are assigned to an asset. This supports the auditing and visibility of the risks to the organisation’s architecture.
Details about these components are stored in the CMDB which you can use to monitor the infrastructure, helping ensure integrity, stability, and continuous service operation. It gives you the central repository of all information which is key to achieving a Zero Trust model.
Greater visibility
ITOM Visibility gives you an accurate, up-to-date view of your IT infrastructure and services, spanning both multi-cloud and on-premise environments. It automates the end-to-end infrastructure discovery and service mapping process—including tracking ongoing changes—creating a complete and reliable record in your CMDB.
This infrastructure and service information is seamlessly leveraged by other ServiceNow applications such as ITOM Health, ITOM Optimization, and Software Asset Management. It can be easily enriched with additional configuration information/items. Software Asset management allows you to see who is using the software, provides approvals for access to software applications and workflows.
SecOps & GRC
Ensuring that your devices are kept up to date with patches can also be done using ServiceNow SecOps and the Vulnerability Response (VR) application. VR helps organisations to identify and quickly respond to vulnerabilities, helping to track, prioritise, and resolve them efficiently using a single platform.
Configuration compliance within ServiceNow SecOps can also help ensure that assets are configured as per the company policy. Improperly configured software can create a risk for the organisation and can go unidentified for a long time. Configuration compliance leverages the CMDB to determine which assets are most critical and using third party security configuration assessment scans can quickly remediate misconfigured devices.
Coordinating the response
ServiceNow’s workflow and automation capabilities can coordinate an IT response, from a single platform to address changes and updates. Configuration compliance can also be fed into the continuous monitoring feature of ServiceNow Governance, Risk and Compliance to further mitigate risk.
There are a number of preventative technologies that can be leveraged, including:
- Identity and access management
- Privileged access management
- Cloud access security broker or policy orchestrator
- SIEM or other user and entity behaviour analytics
- Network segmentation
- Next-generation firewall
As the platform of platforms, ServiceNow provides a unified experience across multiple technologies deployed across the enterprise. ServiceNow has seamless integrations with many of the key vendors working in this space. It brings the ability to leverage the above technologies and add context using the CMDB and ITOM to make the task of identifying high-risk assets much easier. Whilst ServiceNow supports security teams in responding faster there is significant value in its ability to provide a single pane of glass to monitor these various technologies.
Focus your monitoring on devices and services using ServiceNow SecOps. As mentioned above, the platform has the ability to provide a centralised place to capture the information from your security technologies. The platform can utilise that information along with workflows, automation and if possible, orchestration. Moving to this stage of the Zero Trust model can ensure remediation can take place quickly should a breach or attack occur.
By also monitoring your devices, ServiceNow gives you visibility into your organisation’s security posture using detailed dashboards and reports. This visibility over what is baseline will help establish normal behaviour. In turn this can assist with identifying abnormal behaviour, that could be a sign of malicious activity, as is occurs. Using the reports and dashboards can provide administrators with an insight into how well the security tools are working, if anything needs changing or if further automation can be added to further secure the network.
Auditing using the ServiceNow platform
To ensure everything is captured correctly, audit logs should be created automatically. ServiceNow has a dedicated audit table that can be configured to audit a wide range of things and, by default, the system tracks changes to the incident, change and problem tables, among others. The audit information is invaluable in creating the reports to ensure that your security posture is correct.
Implementing a Zero Trust Model
Zero Trust is not a new concept – however it is one that can be implemented using some of the existing technologies already in place within the corporate IT infrastructure.
Starting a Zero Trust architecture is a process that requires careful planning and execution. However, I recommend that you progressively add layers as per the various sections described above, rather than attempting a big bang ‘jump’ to Zero Trust.
Using a platform that can bring lots of disparate systems and information together in one place can help make the transition smoother. For example, a key aspect of the Zero Trust model is knowing what devices, assets, services and users you have and how they work. This is more difficult to attain since large swathes of the workforce began working from home, but the ServiceNow CMDB lets you know exactly what assets are in your IT environment using current, accurate configuration data.
In addition to using existing technologies to achieve Zero Trust Security, new technologies may also be required to feed into this model. Computacenter can provide an agnostic view on the optimum technology to use in each case to help create a Zero Trust architecture and also advise on how to best utilise the existing technologies that you already have.
Only then can you have the confidence to put your faith in a Zero Trust model.